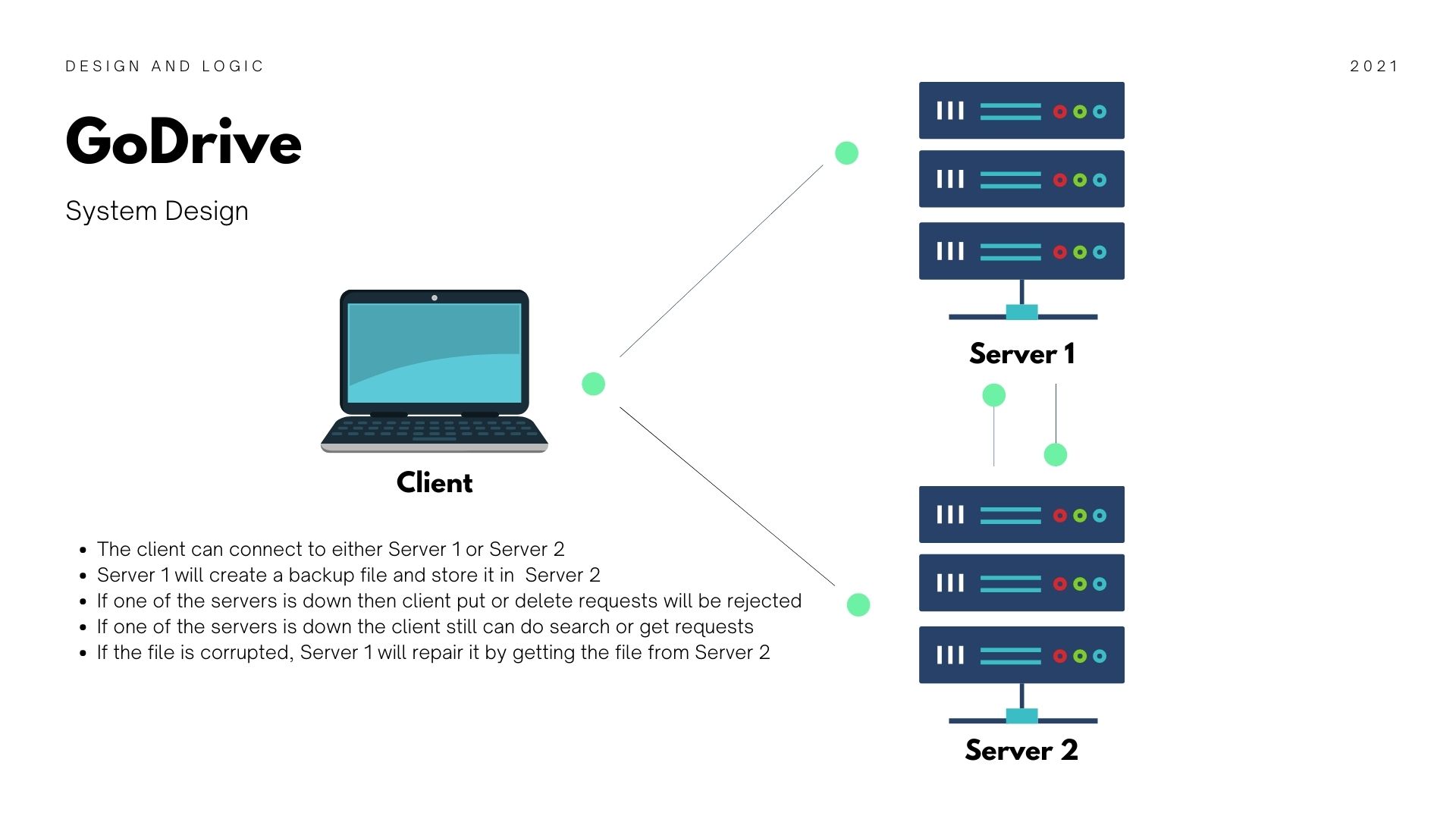
Swift
This package provides an easy to use library for interfacing with Swift / Openstack Object Storage / Rackspace cloud files from the Go Language
See here for package docs
http://godoc.org/github.com/ncw/swift/v2
Install
Use go to install the library
go get github.com/ncw/swift/v2
Usage
See here for full package docs
Here is a short example from the docs
import "github.com/ncw/swift/v2"
// Create a connection
c := swift.Connection{
UserName: "user",
ApiKey: "key",
AuthUrl: "auth_url",
Domain: "domain", // Name of the domain (v3 auth only)
Tenant: "tenant", // Name of the tenant (v2 auth only)
}
// Authenticate
err := c.Authenticate()
if err != nil {
panic(err)
}
// List all the containers
containers, err := c.ContainerNames(nil)
fmt.Println(containers)
// etc...
Migrating from v1
The library has current major version v2. If you want to migrate from the first version of library github.com/ncw/swift you have to explicitly add the /v2 suffix to the imports.
Most of the exported functions were added a new context.Context parameter in the v2, which you will have to provide when migrating.
Additions
The rs sub project contains a wrapper for the Rackspace specific CDN Management interface.
Testing
To run the tests you can either use an embedded fake Swift server either use a real Openstack Swift server or a Rackspace Cloud files account.
When using a real Swift server, you need to set these environment variables before running the tests
export SWIFT_API_USER='user'
export SWIFT_API_KEY='key'
export SWIFT_AUTH_URL='https://url.of.auth.server/v1.0'
And optionally these if using v2 authentication
export SWIFT_TENANT='TenantName'
export SWIFT_TENANT_ID='TenantId'
And optionally these if using v3 authentication
export SWIFT_TENANT='TenantName'
export SWIFT_TENANT_ID='TenantId'
export SWIFT_API_DOMAIN_ID='domain id'
export SWIFT_API_DOMAIN='domain name'
And optionally these if using v3 trust
export SWIFT_TRUST_ID='TrustId'
And optionally this if you want to skip server certificate validation
export SWIFT_AUTH_INSECURE=1
And optionally this to configure the connect channel timeout, in seconds
export SWIFT_CONNECTION_CHANNEL_TIMEOUT=60
And optionally this to configure the data channel timeout, in seconds
export SWIFT_DATA_CHANNEL_TIMEOUT=60
Then run the tests with go test
License
This is free software under the terms of MIT license (check COPYING file included in this package).
Contact and support
The project website is at:
There you can file bug reports, ask for help or contribute patches.
Authors
- Nick Craig-Wood [email protected]
Contributors
- Brian "bojo" Jones [email protected]
- Janika Liiv [email protected]
- Yamamoto, Hirotaka [email protected]
- Stephen [email protected]
- platformpurple [email protected]
- Paul Querna [email protected]
- Livio Soares [email protected]
- thesyncim [email protected]
- lsowen [email protected] [email protected]
- Sylvain Baubeau [email protected]
- Chris Kastorff [email protected]
- Dai HaoJun [email protected]
- Hua Wang [email protected]
- Fabian Ruff [email protected] [email protected]
- Arturo Reuschenbach Puncernau [email protected]
- Petr Kotek [email protected]
- Stefan Majewsky [email protected] [email protected]
- Cezar Sa Espinola [email protected]
- Sam Gunaratne [email protected]
- Richard Scothern [email protected]
- Michel Couillard [email protected]
- Christopher Waldon [email protected]
- dennis [email protected]
- hag [email protected]
- Alexander Neumann [email protected]
- eclipseo [email protected]
- Yuri Per [email protected]
- Falk Reimann [email protected]
- Arthur Paim Arnold [email protected]
- Bruno Michel [email protected]
- Charles Hsu [email protected]
- Omar Ali [email protected]
- Andreas Andersen [email protected]
- kayrus [email protected]
- CodeLingo Bot [email protected]
- Jérémy Clerc [email protected]
- 4xicom [email protected]
- Bo [email protected]
- Thiago da Silva [email protected]
- Brandon WELSCH [email protected]
- Damien Tournoud [email protected]
- Pedro Kiefer [email protected]
- Martin Chodur [email protected]
- Devendra [email protected]