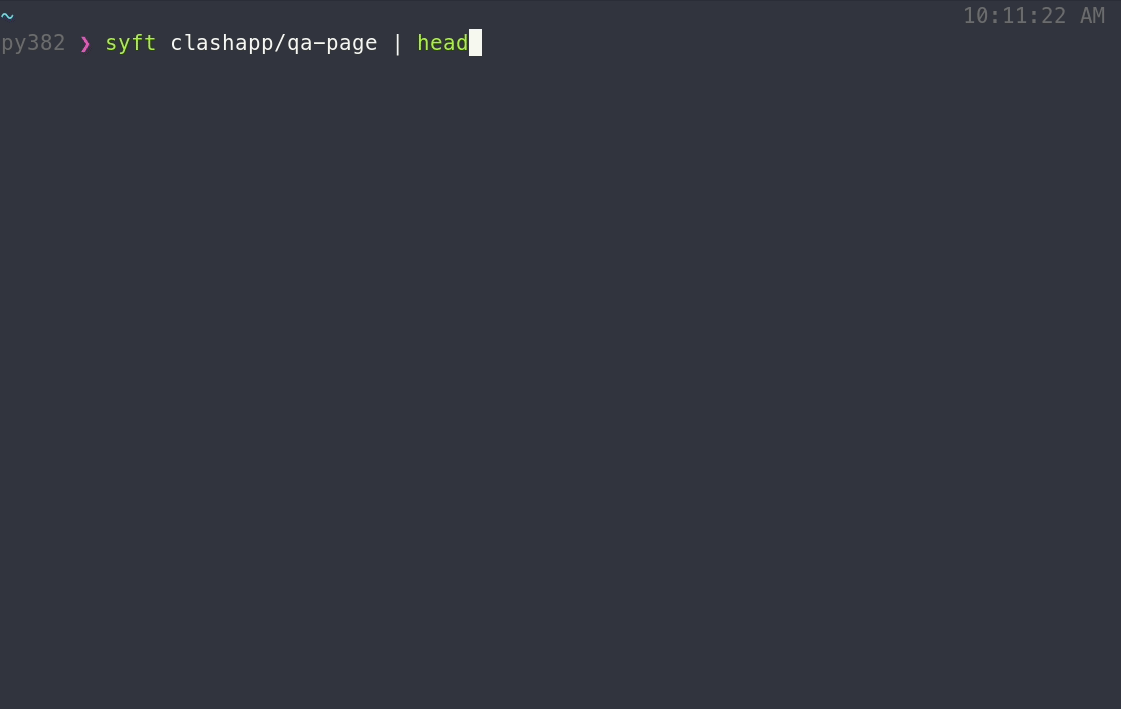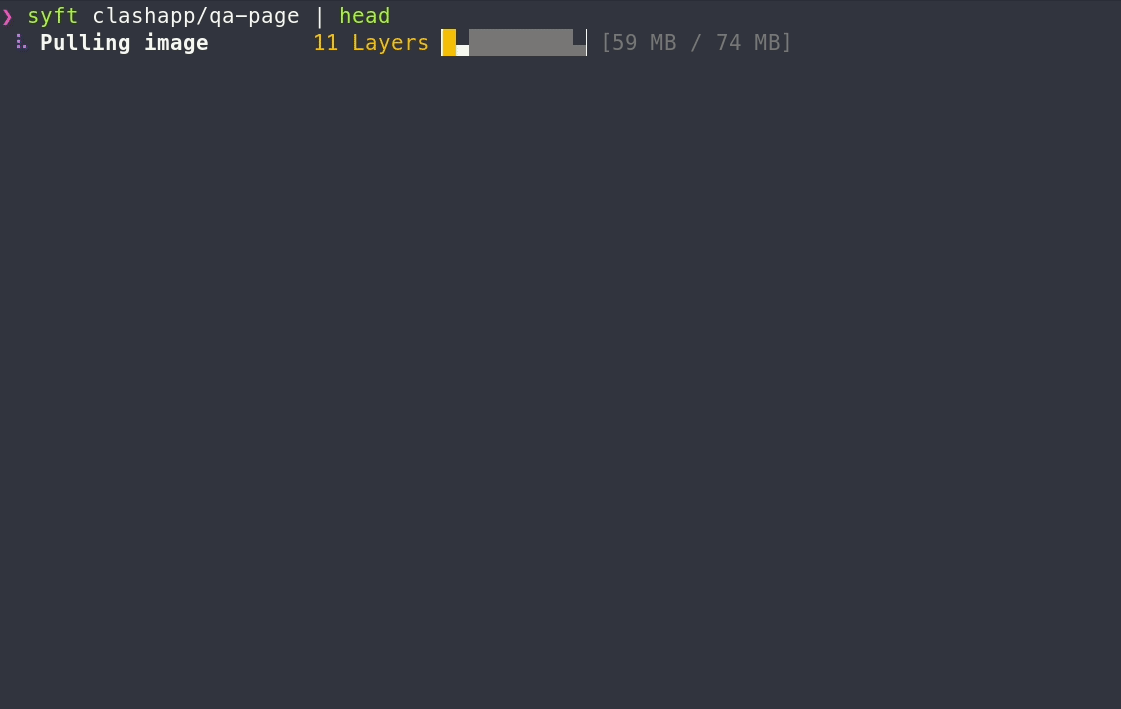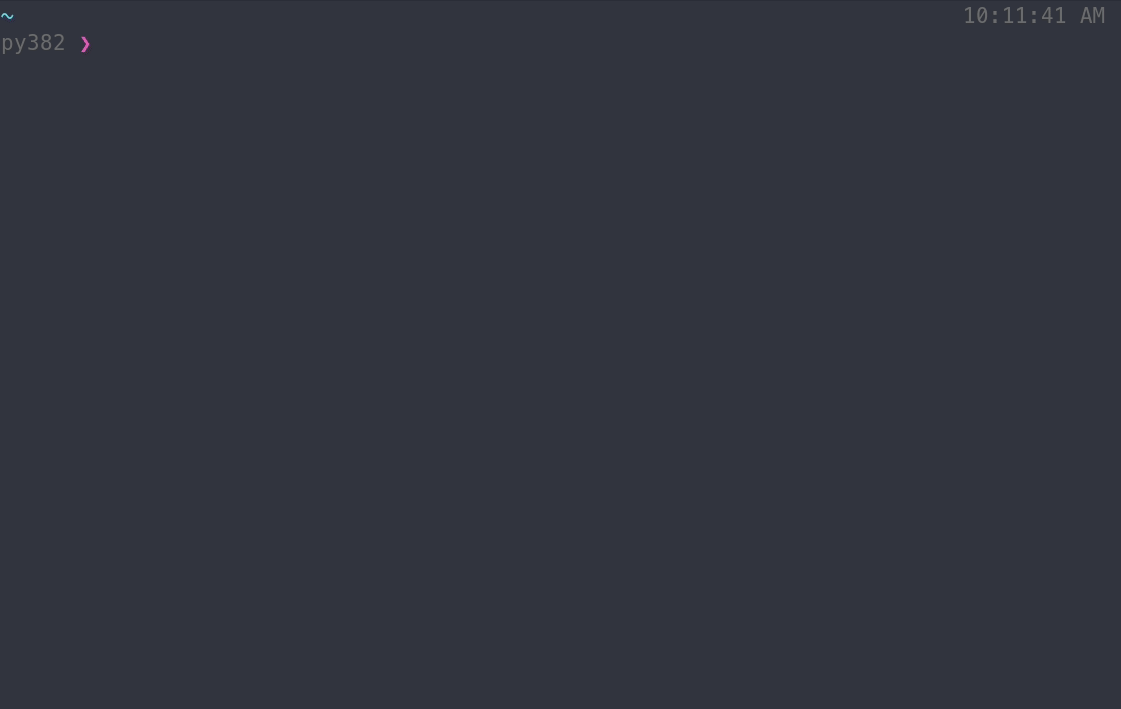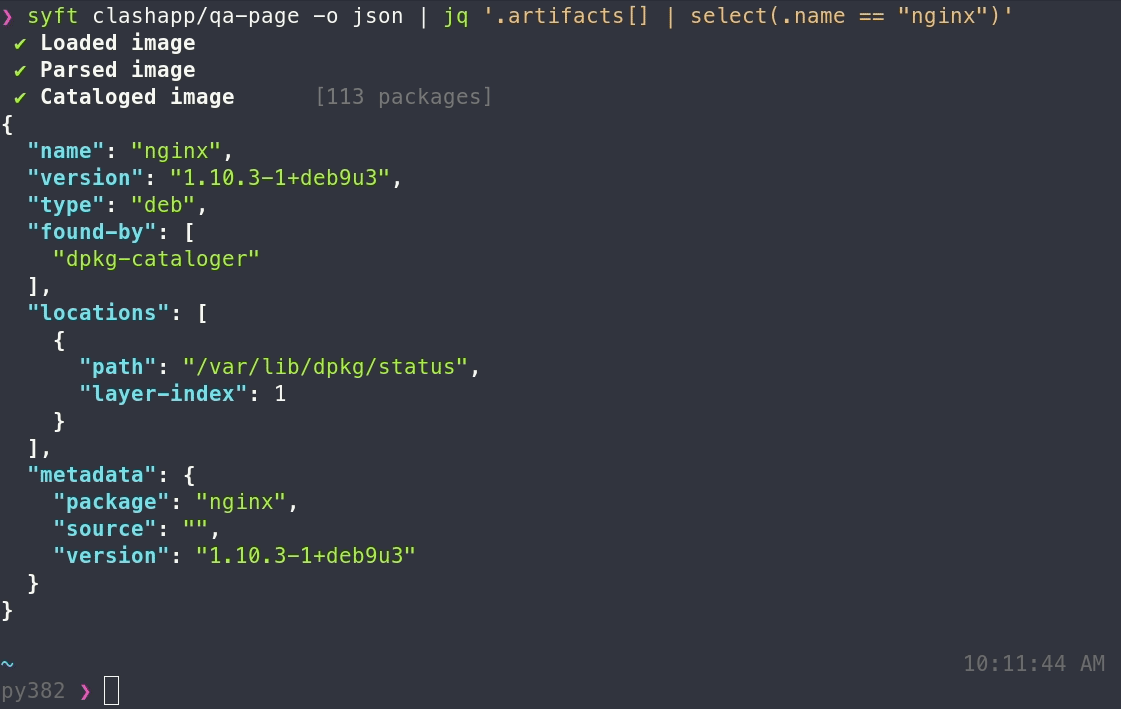
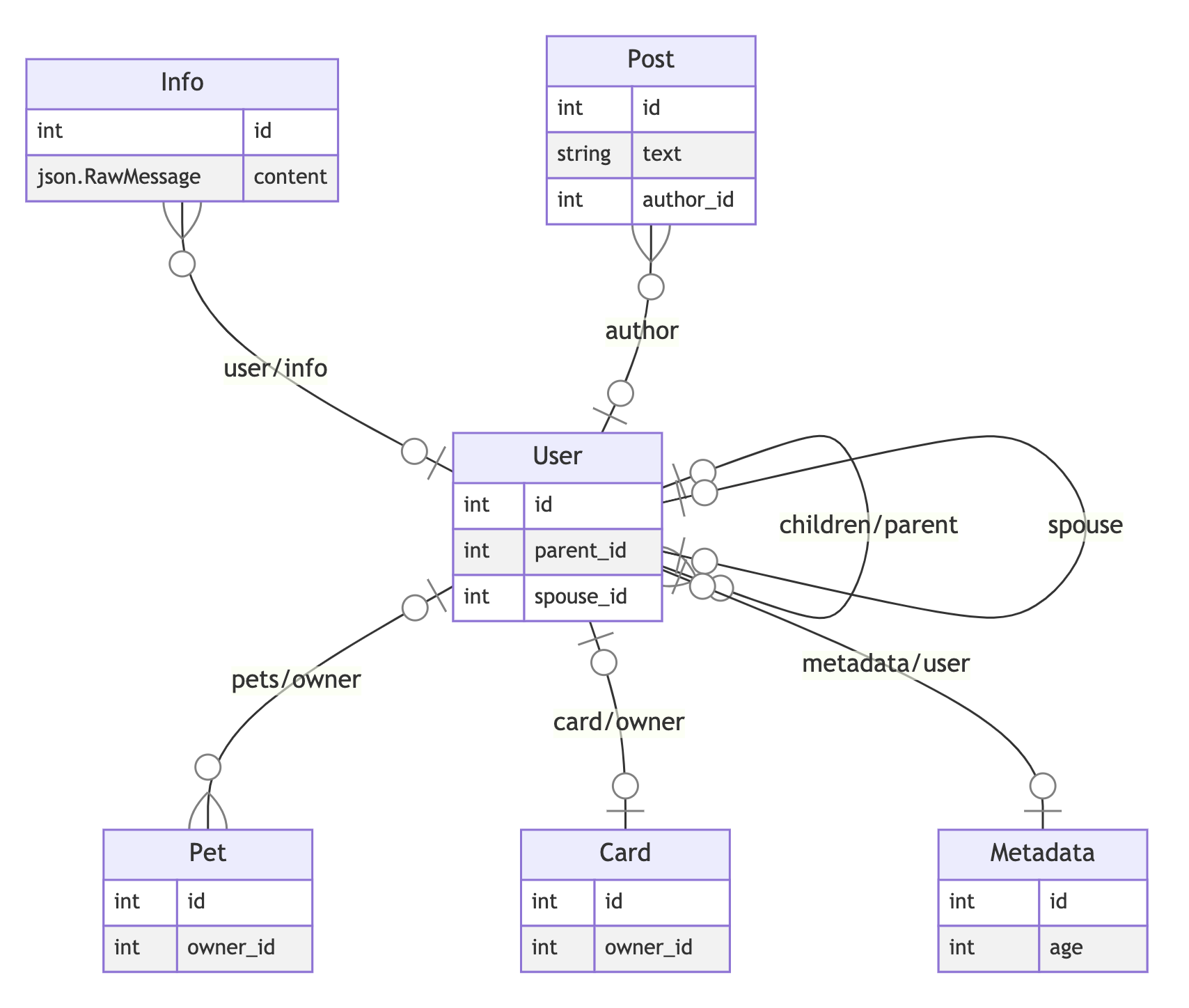
SPDX-json from go-integration
{
"SPDXID": "SPDXRef-DOCUMENT",
"name": "/tmp/sha256_21a3deaa0d32a8057914f36584b5288d2e5ecc984380bc0118285c70fa8c9300.tar.gz",
"spdxVersion": "SPDX-2.2",
"creationInfo": {
"created": "2022-09-18T08:20:02.269681097Z",
"creators": [
"Organization: Anchore, Inc",
"Tool: syft-v9.9.9"
],
"licenseListVersion": "3.18"
},
"dataLicense": "CC0-1.0",
"documentNamespace": "https://anchore.com/syft/image/tmp/sha256_21a3deaa0d32a8057914f36584b5288d2e5ecc984380bc0118285c70fa8c9300.tar.gz-480350d2-9f14-4665-b9b6-737b6333a21a",
"packages": [
{
"SPDXID": "SPDXRef-9f527213f4d2a873",
"name": "alpine-baselayout",
"licenseConcluded": "GPL-2.0-only",
"description": "Alpine base dir structure and init scripts",
"downloadLocation": "https://git.alpinelinux.org/cgit/aports/tree/main/alpine-baselayout",
"externalRefs": [
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:alpine-baselayout:alpine-baselayout:3.2.0-r18:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:alpine-baselayout:alpine_baselayout:3.2.0-r18:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:alpine_baselayout:alpine-baselayout:3.2.0-r18:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:alpine_baselayout:alpine_baselayout:3.2.0-r18:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:alpine:alpine-baselayout:3.2.0-r18:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:alpine:alpine_baselayout:3.2.0-r18:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "PACKAGE_MANAGER",
"referenceLocator": "pkg:alpine/[email protected]?arch=x86_64&upstream=alpine-baselayout&distro=alpine-3.15.0",
"referenceType": "purl"
}
],
"filesAnalyzed": false,
"hasFiles": [
"SPDXRef-2eaa15c5fc625ebe",
"SPDXRef-a53373020dfa8bb4",
"SPDXRef-38605c90f707fb90",
"SPDXRef-60fa740c32339374",
"SPDXRef-24d0f8d913cd9906",
"SPDXRef-d41a5f82a774a6a1",
"SPDXRef-13d6d27618d264f7",
"SPDXRef-b499705c36475f74",
"SPDXRef-2e3613b244458b5a",
"SPDXRef-84fd54b3f2a2e825",
"SPDXRef-32701f6d1e056c29",
"SPDXRef-93b858998f2c7034",
"SPDXRef-fb021b79aa9cd553",
"SPDXRef-82fda88ae28dd50",
"SPDXRef-9ab25fdcabefa4ac",
"SPDXRef-2c0eaf2a7d7dbad",
"SPDXRef-f3ee626693308800",
"SPDXRef-420fa6f3289d6ee6",
"SPDXRef-ae2cba512a3f4065",
"SPDXRef-b3a5f05adcd1cf82",
"SPDXRef-64b20ab568341372",
"SPDXRef-5e12c5188eeb9cb3",
"SPDXRef-18d9a7fcef583aeb",
"SPDXRef-dc65dbf355556024"
],
"licenseDeclared": "GPL-2.0-only",
"originator": "Person: Natanael Copa <[email protected]>",
"sourceInfo": "acquired package info from APK DB: /lib/apk/db/installed",
"versionInfo": "3.2.0-r18"
},
{
"SPDXID": "SPDXRef-1a72ca3b88e1b67e",
"name": "alpine-keys",
"licenseConcluded": "MIT",
"description": "Public keys for Alpine Linux packages",
"downloadLocation": "https://alpinelinux.org",
"externalRefs": [
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:alpine-keys:alpine-keys:2.4-r1:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:alpine-keys:alpine_keys:2.4-r1:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:alpine_keys:alpine-keys:2.4-r1:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:alpine_keys:alpine_keys:2.4-r1:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:alpine:alpine-keys:2.4-r1:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:alpine:alpine_keys:2.4-r1:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "PACKAGE_MANAGER",
"referenceLocator": "pkg:alpine/[email protected]?arch=x86_64&upstream=alpine-keys&distro=alpine-3.15.0",
"referenceType": "purl"
}
],
"filesAnalyzed": false,
"hasFiles": [
"SPDXRef-ccc2b3e76affde68",
"SPDXRef-3562d93285c5a3c5",
"SPDXRef-27d8de5355fdb7ba",
"SPDXRef-ff0560ee36b984a7",
"SPDXRef-79cc1d44454e11b9",
"SPDXRef-56080e31fd12fe67",
"SPDXRef-7803dc5a1a496765",
"SPDXRef-57149f915867bf12",
"SPDXRef-2363acec0a71a382",
"SPDXRef-8ec9dcf9b3d1d7ce",
"SPDXRef-39dcc03ca17480ca",
"SPDXRef-496698ff67ca49fc",
"SPDXRef-66756a275982c586",
"SPDXRef-4d646d694b6380fc",
"SPDXRef-add734ec170033bd",
"SPDXRef-abfd85d1b45289dc",
"SPDXRef-2dac0f0b0463195c",
"SPDXRef-f059a81847acaad9",
"SPDXRef-395f72182f48f77c",
"SPDXRef-187efc434122356a",
"SPDXRef-59d943ecba7b9db1",
"SPDXRef-2c8a8c151837aa6e"
],
"licenseDeclared": "MIT",
"originator": "Person: Natanael Copa <[email protected]>",
"sourceInfo": "acquired package info from APK DB: /lib/apk/db/installed",
"versionInfo": "2.4-r1"
},
{
"SPDXID": "SPDXRef-1c6e057c6965bdd6",
"name": "apk-tools",
"licenseConcluded": "GPL-2.0-only",
"description": "Alpine Package Keeper - package manager for alpine",
"downloadLocation": "https://gitlab.alpinelinux.org/alpine/apk-tools",
"externalRefs": [
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:apk-tools:apk-tools:2.12.7-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:apk-tools:apk_tools:2.12.7-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:apk_tools:apk-tools:2.12.7-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:apk_tools:apk_tools:2.12.7-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:apk:apk-tools:2.12.7-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:apk:apk_tools:2.12.7-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "PACKAGE_MANAGER",
"referenceLocator": "pkg:alpine/[email protected]?arch=x86_64&upstream=apk-tools&distro=alpine-3.15.0",
"referenceType": "purl"
}
],
"filesAnalyzed": false,
"hasFiles": [
"SPDXRef-5f14b5421fba85af",
"SPDXRef-d72447617fa2b70c"
],
"licenseDeclared": "GPL-2.0-only",
"originator": "Person: Natanael Copa <[email protected]>",
"sourceInfo": "acquired package info from APK DB: /lib/apk/db/installed",
"versionInfo": "2.12.7-r3"
},
{
"SPDXID": "SPDXRef-2e32896982ce9587",
"name": "busybox",
"licenseConcluded": "GPL-2.0-only",
"description": "Size optimized toolbox of many common UNIX utilities",
"downloadLocation": "https://busybox.net/",
"externalRefs": [
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:busybox:busybox:1.34.1-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "PACKAGE_MANAGER",
"referenceLocator": "pkg:alpine/[email protected]?arch=x86_64&upstream=busybox&distro=alpine-3.15.0",
"referenceType": "purl"
}
],
"filesAnalyzed": false,
"hasFiles": [
"SPDXRef-be5355441673f6dc",
"SPDXRef-e7d6b30bf31f933a",
"SPDXRef-e6d162458c0b30b0",
"SPDXRef-d5ee1ce0839cb21a",
"SPDXRef-988a54d89f5c4c09",
"SPDXRef-cd1c702a19149d7d"
],
"licenseDeclared": "GPL-2.0-only",
"originator": "Person: Natanael Copa <[email protected]>",
"sourceInfo": "acquired package info from APK DB: /lib/apk/db/installed",
"versionInfo": "1.34.1-r3"
},
{
"SPDXID": "SPDXRef-9bb0a989e24e7661",
"name": "ca-certificates-bundle",
"licenseConcluded": "MPL-2.0 AND MIT",
"description": "Pre generated bundle of Mozilla certificates",
"downloadLocation": "https://www.mozilla.org/en-US/about/governance/policies/security-group/certs/",
"externalRefs": [
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:ca-certificates-bundle:ca-certificates-bundle:20191127-r7:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:ca-certificates-bundle:ca_certificates_bundle:20191127-r7:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:ca_certificates_bundle:ca-certificates-bundle:20191127-r7:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:ca_certificates_bundle:ca_certificates_bundle:20191127-r7:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:ca-certificates:ca-certificates-bundle:20191127-r7:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:ca-certificates:ca_certificates_bundle:20191127-r7:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:ca_certificates:ca-certificates-bundle:20191127-r7:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:ca_certificates:ca_certificates_bundle:20191127-r7:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:ca:ca-certificates-bundle:20191127-r7:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:ca:ca_certificates_bundle:20191127-r7:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "PACKAGE_MANAGER",
"referenceLocator": "pkg:alpine/ca-certificates-bundle@20191127-r7?arch=x86_64&upstream=ca-certificates&distro=alpine-3.15.0",
"referenceType": "purl"
}
],
"filesAnalyzed": false,
"hasFiles": [
"SPDXRef-b7cfa7f53a05225f"
],
"licenseDeclared": "MPL-2.0 AND MIT",
"originator": "Person: Natanael Copa <[email protected]>",
"sourceInfo": "acquired package info from APK DB: /lib/apk/db/installed",
"versionInfo": "20191127-r7"
},
{
"SPDXID": "SPDXRef-e87a79fdaecaabd2",
"name": "libc-utils",
"licenseConcluded": "BSD-2-Clause AND BSD-3-Clause",
"description": "Meta package to pull in correct libc",
"downloadLocation": "https://alpinelinux.org",
"externalRefs": [
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:libc-utils:libc-utils:0.7.2-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:libc-utils:libc_utils:0.7.2-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:libc_utils:libc-utils:0.7.2-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:libc_utils:libc_utils:0.7.2-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:libc:libc-utils:0.7.2-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:libc:libc_utils:0.7.2-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "PACKAGE_MANAGER",
"referenceLocator": "pkg:alpine/[email protected]?arch=x86_64&upstream=libc-dev&distro=alpine-3.15.0",
"referenceType": "purl"
}
],
"filesAnalyzed": false,
"licenseDeclared": "BSD-2-Clause AND BSD-3-Clause",
"originator": "Person: Natanael Copa <[email protected]>",
"sourceInfo": "acquired package info from APK DB: /lib/apk/db/installed",
"versionInfo": "0.7.2-r3"
},
{
"SPDXID": "SPDXRef-873ddd0587a8ac17",
"name": "libcrypto1.1",
"licenseConcluded": "OpenSSL",
"description": "Crypto library from openssl",
"downloadLocation": "https://www.openssl.org/",
"externalRefs": [
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:libcrypto1.1:libcrypto1.1:1.1.1l-r7:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "PACKAGE_MANAGER",
"referenceLocator": "pkg:alpine/[email protected]?arch=x86_64&upstream=openssl&distro=alpine-3.15.0",
"referenceType": "purl"
}
],
"filesAnalyzed": false,
"hasFiles": [
"SPDXRef-4862e08252039e5",
"SPDXRef-f57c06db35618298",
"SPDXRef-ba1b2107c3063563",
"SPDXRef-b7cfa7f53a05225f",
"SPDXRef-d1029b42eed49dbe",
"SPDXRef-5f7354d1f6e1cdce",
"SPDXRef-1a7b85af7f458360",
"SPDXRef-a00e69b6cf4b0ef0"
],
"licenseDeclared": "OpenSSL",
"originator": "Person: Timo Teras <[email protected]>",
"sourceInfo": "acquired package info from APK DB: /lib/apk/db/installed",
"versionInfo": "1.1.1l-r7"
},
{
"SPDXID": "SPDXRef-484b9eacc3ccdd48",
"name": "libretls",
"licenseConcluded": "ISC",
"description": "port of libtls from libressl to openssl",
"downloadLocation": "https://git.causal.agency/libretls/",
"externalRefs": [
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:libretls:libretls:3.3.4-r2:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "PACKAGE_MANAGER",
"referenceLocator": "pkg:alpine/[email protected]?arch=x86_64&upstream=libretls&distro=alpine-3.15.0",
"referenceType": "purl"
}
],
"filesAnalyzed": false,
"hasFiles": [
"SPDXRef-81250f1630c1a804"
],
"licenseDeclared": "ISC",
"originator": "Person: Ariadne Conill <[email protected]>",
"sourceInfo": "acquired package info from APK DB: /lib/apk/db/installed",
"versionInfo": "3.3.4-r2"
},
{
"SPDXID": "SPDXRef-7d62dc5b1a20803f",
"name": "libssl1.1",
"licenseConcluded": "OpenSSL",
"description": "SSL shared libraries",
"downloadLocation": "https://www.openssl.org/",
"externalRefs": [
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:libssl1.1:libssl1.1:1.1.1l-r7:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "PACKAGE_MANAGER",
"referenceLocator": "pkg:alpine/[email protected]?arch=x86_64&upstream=openssl&distro=alpine-3.15.0",
"referenceType": "purl"
}
],
"filesAnalyzed": false,
"hasFiles": [
"SPDXRef-a64a40d78e73f3bd"
],
"licenseDeclared": "OpenSSL",
"originator": "Person: Timo Teras <[email protected]>",
"sourceInfo": "acquired package info from APK DB: /lib/apk/db/installed",
"versionInfo": "1.1.1l-r7"
},
{
"SPDXID": "SPDXRef-20dc20cbb6dbea6",
"name": "musl",
"licenseConcluded": "MIT",
"description": "the musl c library (libc) implementation",
"downloadLocation": "https://musl.libc.org/",
"externalRefs": [
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:musl:musl:1.2.2-r7:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "PACKAGE_MANAGER",
"referenceLocator": "pkg:alpine/[email protected]?arch=x86_64&upstream=musl&distro=alpine-3.15.0",
"referenceType": "purl"
}
],
"filesAnalyzed": false,
"hasFiles": [
"SPDXRef-e322847d6485c76d"
],
"licenseDeclared": "MIT",
"originator": "Person: Timo Teräs <[email protected]>",
"sourceInfo": "acquired package info from APK DB: /lib/apk/db/installed",
"versionInfo": "1.2.2-r7"
},
{
"SPDXID": "SPDXRef-35c3680577fae0df",
"name": "musl-utils",
"licenseConcluded": "MIT",
"description": "the musl c library (libc) implementation",
"downloadLocation": "https://musl.libc.org/",
"externalRefs": [
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:musl-utils:musl-utils:1.2.2-r7:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:musl-utils:musl_utils:1.2.2-r7:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:musl_utils:musl-utils:1.2.2-r7:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:musl_utils:musl_utils:1.2.2-r7:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:musl:musl-utils:1.2.2-r7:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:musl:musl_utils:1.2.2-r7:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "PACKAGE_MANAGER",
"referenceLocator": "pkg:alpine/[email protected]?arch=x86_64&upstream=musl&distro=alpine-3.15.0",
"referenceType": "purl"
}
],
"filesAnalyzed": false,
"hasFiles": [
"SPDXRef-780fcf6f56cca2e0",
"SPDXRef-ab2d028a906db5df",
"SPDXRef-8e69e89855b5ae0f",
"SPDXRef-d59e19c68624688f",
"SPDXRef-757b30be1d3baa0b"
],
"licenseDeclared": "MIT",
"originator": "Person: Timo Teräs <[email protected]>",
"sourceInfo": "acquired package info from APK DB: /lib/apk/db/installed",
"versionInfo": "1.2.2-r7"
},
{
"SPDXID": "SPDXRef-f2d426372356602d",
"name": "scanelf",
"licenseConcluded": "GPL-2.0-only",
"description": "Scan ELF binaries for stuff",
"downloadLocation": "https://wiki.gentoo.org/wiki/Hardened/PaX_Utilities",
"externalRefs": [
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:scanelf:scanelf:1.3.3-r0:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "PACKAGE_MANAGER",
"referenceLocator": "pkg:alpine/[email protected]?arch=x86_64&upstream=pax-utils&distro=alpine-3.15.0",
"referenceType": "purl"
}
],
"filesAnalyzed": false,
"hasFiles": [
"SPDXRef-7516f5d905deb6db"
],
"licenseDeclared": "GPL-2.0-only",
"originator": "Person: Natanael Copa <[email protected]>",
"sourceInfo": "acquired package info from APK DB: /lib/apk/db/installed",
"versionInfo": "1.3.3-r0"
},
{
"SPDXID": "SPDXRef-38bc092600723894",
"name": "ssl_client",
"licenseConcluded": "GPL-2.0-only",
"description": "EXternal ssl_client for busybox wget",
"downloadLocation": "https://busybox.net/",
"externalRefs": [
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:ssl-client:ssl-client:1.34.1-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:ssl-client:ssl_client:1.34.1-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:ssl_client:ssl-client:1.34.1-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:ssl_client:ssl_client:1.34.1-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:ssl:ssl-client:1.34.1-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:ssl:ssl_client:1.34.1-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "PACKAGE_MANAGER",
"referenceLocator": "pkg:alpine/[email protected]?arch=x86_64&upstream=busybox&distro=alpine-3.15.0",
"referenceType": "purl"
}
],
"filesAnalyzed": false,
"hasFiles": [
"SPDXRef-711694a1725d661e"
],
"licenseDeclared": "GPL-2.0-only",
"originator": "Person: Natanael Copa <[email protected]>",
"sourceInfo": "acquired package info from APK DB: /lib/apk/db/installed",
"versionInfo": "1.34.1-r3"
},
{
"SPDXID": "SPDXRef-50d3560550c47774",
"name": "zlib",
"licenseConcluded": "Zlib",
"description": "A compression/decompression Library",
"downloadLocation": "https://zlib.net/",
"externalRefs": [
{
"referenceCategory": "SECURITY",
"referenceLocator": "cpe:2.3:a:zlib:zlib:1.2.11-r3:*:*:*:*:*:*:*",
"referenceType": "cpe23Type"
},
{
"referenceCategory": "PACKAGE_MANAGER",
"referenceLocator": "pkg:alpine/[email protected]?arch=x86_64&upstream=zlib&distro=alpine-3.15.0",
"referenceType": "purl"
}
],
"filesAnalyzed": false,
"hasFiles": [
"SPDXRef-bfd3d0235da50adb"
],
"licenseDeclared": "Zlib",
"originator": "Person: Natanael Copa <[email protected]>",
"sourceInfo": "acquired package info from APK DB: /lib/apk/db/installed",
"versionInfo": "1.2.11-r3"
}
],
"files": [
{
"SPDXID": "SPDXRef-988a54d89f5c4c09",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/bin/busybox"
},
{
"SPDXID": "SPDXRef-8ec9dcf9b3d1d7ce",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-39dcc03ca17480ca",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-4d646d694b6380fc",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-395f72182f48f77c",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-496698ff67ca49fc",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-2eaa15c5fc625ebe",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/crontabs/root"
},
{
"SPDXID": "SPDXRef-a53373020dfa8bb4",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/fstab"
},
{
"SPDXID": "SPDXRef-2c0eaf2a7d7dbad",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/group"
},
{
"SPDXID": "SPDXRef-f3ee626693308800",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/hostname"
},
{
"SPDXID": "SPDXRef-38605c90f707fb90",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/hosts"
},
{
"SPDXID": "SPDXRef-60fa740c32339374",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/inittab"
},
{
"SPDXID": "SPDXRef-cd1c702a19149d7d",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/logrotate.d/acpid"
},
{
"SPDXID": "SPDXRef-420fa6f3289d6ee6",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/modprobe.d/aliases.conf"
},
{
"SPDXID": "SPDXRef-ae2cba512a3f4065",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/modprobe.d/blacklist.conf"
},
{
"SPDXID": "SPDXRef-24d0f8d913cd9906",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/modprobe.d/i386.conf"
},
{
"SPDXID": "SPDXRef-d41a5f82a774a6a1",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/modprobe.d/kms.conf"
},
{
"SPDXID": "SPDXRef-dc65dbf355556024",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/modules"
},
{
"SPDXID": "SPDXRef-b3a5f05adcd1cf82",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/motd"
},
{
"SPDXID": "SPDXRef-be5355441673f6dc",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/network/if-up.d/dad"
},
{
"SPDXID": "SPDXRef-b499705c36475f74",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/passwd"
},
{
"SPDXID": "SPDXRef-2e3613b244458b5a",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/profile"
},
{
"SPDXID": "SPDXRef-64b20ab568341372",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/profile.d/README"
},
{
"SPDXID": "SPDXRef-84fd54b3f2a2e825",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/profile.d/color_prompt.sh.disabled"
},
{
"SPDXID": "SPDXRef-32701f6d1e056c29",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/profile.d/locale.sh"
},
{
"SPDXID": "SPDXRef-5e12c5188eeb9cb3",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/protocols"
},
{
"SPDXID": "SPDXRef-e7d6b30bf31f933a",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/securetty"
},
{
"SPDXID": "SPDXRef-9ab25fdcabefa4ac",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/services"
},
{
"SPDXID": "SPDXRef-18d9a7fcef583aeb",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/shadow"
},
{
"SPDXID": "SPDXRef-93b858998f2c7034",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/shells"
},
{
"SPDXID": "SPDXRef-b7cfa7f53a05225f",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/ssl/certs/ca-certificates.crt"
},
{
"SPDXID": "SPDXRef-d1029b42eed49dbe",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/ssl1.1/ct_log_list.cnf.dist"
},
{
"SPDXID": "SPDXRef-5f7354d1f6e1cdce",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/ssl1.1/openssl.cnf"
},
{
"SPDXID": "SPDXRef-1a7b85af7f458360",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/ssl1.1/openssl.cnf.dist"
},
{
"SPDXID": "SPDXRef-fb021b79aa9cd553",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/sysctl.conf"
},
{
"SPDXID": "SPDXRef-e6d162458c0b30b0",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/etc/udhcpd.conf"
},
{
"SPDXID": "SPDXRef-e322847d6485c76d",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/lib/ld-musl-x86_64.so.1"
},
{
"SPDXID": "SPDXRef-5f14b5421fba85af",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/lib/libapk.so.3.12.0"
},
{
"SPDXID": "SPDXRef-a00e69b6cf4b0ef0",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/lib/libcrypto.so.1.1"
},
{
"SPDXID": "SPDXRef-a64a40d78e73f3bd",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/lib/libssl.so.1.1"
},
{
"SPDXID": "SPDXRef-bfd3d0235da50adb",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/lib/libz.so.1.2.11"
},
{
"SPDXID": "SPDXRef-82fda88ae28dd50",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/lib/sysctl.d/00-alpine.conf"
},
{
"SPDXID": "SPDXRef-d72447617fa2b70c",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/sbin/apk"
},
{
"SPDXID": "SPDXRef-d59e19c68624688f",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/sbin/ldconfig"
},
{
"SPDXID": "SPDXRef-13d6d27618d264f7",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/sbin/mkmntdirs"
},
{
"SPDXID": "SPDXRef-757b30be1d3baa0b",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/bin/getconf"
},
{
"SPDXID": "SPDXRef-780fcf6f56cca2e0",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/bin/getent"
},
{
"SPDXID": "SPDXRef-ab2d028a906db5df",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/bin/iconv"
},
{
"SPDXID": "SPDXRef-8e69e89855b5ae0f",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/bin/ldd"
},
{
"SPDXID": "SPDXRef-7516f5d905deb6db",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/bin/scanelf"
},
{
"SPDXID": "SPDXRef-711694a1725d661e",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/bin/ssl_client"
},
{
"SPDXID": "SPDXRef-4862e08252039e5",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/lib/engines-1.1/afalg.so"
},
{
"SPDXID": "SPDXRef-f57c06db35618298",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/lib/engines-1.1/capi.so"
},
{
"SPDXID": "SPDXRef-ba1b2107c3063563",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/lib/engines-1.1/padlock.so"
},
{
"SPDXID": "SPDXRef-81250f1630c1a804",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/lib/libtls.so.2.0.3"
},
{
"SPDXID": "SPDXRef-add734ec170033bd",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/share/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-59d943ecba7b9db1",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/share/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-27d8de5355fdb7ba",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/share/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-ff0560ee36b984a7",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/share/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-66756a275982c586",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/share/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-2c8a8c151837aa6e",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/share/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-79cc1d44454e11b9",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/share/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-abfd85d1b45289dc",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/share/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-56080e31fd12fe67",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/share/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-7803dc5a1a496765",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/share/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-ccc2b3e76affde68",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/share/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-3562d93285c5a3c5",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/share/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-57149f915867bf12",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/share/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-2363acec0a71a382",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/share/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-2dac0f0b0463195c",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/share/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-187efc434122356a",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/share/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-f059a81847acaad9",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/share/apk/keys/[email protected]"
},
{
"SPDXID": "SPDXRef-d5ee1ce0839cb21a",
"comment": "layerID: sha256:8d3ac3489996423f53d6087c81180006263b79f206d3fdec9e66f0e27ceb8759",
"licenseConcluded": "NOASSERTION",
"fileName": "/usr/share/udhcpc/default.script"
}
],
"relationships": [
{
"spdxElementId": "SPDXRef-20dc20cbb6dbea6",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-e322847d6485c76d"
},
{
"spdxElementId": "SPDXRef-2e32896982ce9587",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-be5355441673f6dc"
},
{
"spdxElementId": "SPDXRef-2e32896982ce9587",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-e7d6b30bf31f933a"
},
{
"spdxElementId": "SPDXRef-2e32896982ce9587",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-e6d162458c0b30b0"
},
{
"spdxElementId": "SPDXRef-2e32896982ce9587",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-d5ee1ce0839cb21a"
},
{
"spdxElementId": "SPDXRef-2e32896982ce9587",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-988a54d89f5c4c09"
},
{
"spdxElementId": "SPDXRef-2e32896982ce9587",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-cd1c702a19149d7d"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-2eaa15c5fc625ebe"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-a53373020dfa8bb4"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-38605c90f707fb90"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-60fa740c32339374"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-24d0f8d913cd9906"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-d41a5f82a774a6a1"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-13d6d27618d264f7"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-b499705c36475f74"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-2e3613b244458b5a"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-84fd54b3f2a2e825"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-32701f6d1e056c29"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-93b858998f2c7034"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-fb021b79aa9cd553"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-82fda88ae28dd50"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-9ab25fdcabefa4ac"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-2c0eaf2a7d7dbad"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-f3ee626693308800"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-420fa6f3289d6ee6"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-ae2cba512a3f4065"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-b3a5f05adcd1cf82"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-64b20ab568341372"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-5e12c5188eeb9cb3"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-18d9a7fcef583aeb"
},
{
"spdxElementId": "SPDXRef-9f527213f4d2a873",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-dc65dbf355556024"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-ccc2b3e76affde68"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-3562d93285c5a3c5"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-27d8de5355fdb7ba"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-ff0560ee36b984a7"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-79cc1d44454e11b9"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-56080e31fd12fe67"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-7803dc5a1a496765"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-57149f915867bf12"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-2363acec0a71a382"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-8ec9dcf9b3d1d7ce"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-39dcc03ca17480ca"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-496698ff67ca49fc"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-66756a275982c586"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-4d646d694b6380fc"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-add734ec170033bd"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-abfd85d1b45289dc"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-2dac0f0b0463195c"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-f059a81847acaad9"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-395f72182f48f77c"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-187efc434122356a"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-59d943ecba7b9db1"
},
{
"spdxElementId": "SPDXRef-1a72ca3b88e1b67e",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-2c8a8c151837aa6e"
},
{
"spdxElementId": "SPDXRef-9bb0a989e24e7661",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-b7cfa7f53a05225f"
},
{
"spdxElementId": "SPDXRef-873ddd0587a8ac17",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-4862e08252039e5"
},
{
"spdxElementId": "SPDXRef-873ddd0587a8ac17",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-f57c06db35618298"
},
{
"spdxElementId": "SPDXRef-873ddd0587a8ac17",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-ba1b2107c3063563"
},
{
"spdxElementId": "SPDXRef-873ddd0587a8ac17",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-b7cfa7f53a05225f"
},
{
"spdxElementId": "SPDXRef-873ddd0587a8ac17",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-d1029b42eed49dbe"
},
{
"spdxElementId": "SPDXRef-873ddd0587a8ac17",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-5f7354d1f6e1cdce"
},
{
"spdxElementId": "SPDXRef-873ddd0587a8ac17",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-1a7b85af7f458360"
},
{
"spdxElementId": "SPDXRef-873ddd0587a8ac17",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-a00e69b6cf4b0ef0"
},
{
"spdxElementId": "SPDXRef-7d62dc5b1a20803f",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-a64a40d78e73f3bd"
},
{
"spdxElementId": "SPDXRef-484b9eacc3ccdd48",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-81250f1630c1a804"
},
{
"spdxElementId": "SPDXRef-38bc092600723894",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-711694a1725d661e"
},
{
"spdxElementId": "SPDXRef-50d3560550c47774",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-bfd3d0235da50adb"
},
{
"spdxElementId": "SPDXRef-1c6e057c6965bdd6",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-5f14b5421fba85af"
},
{
"spdxElementId": "SPDXRef-1c6e057c6965bdd6",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-d72447617fa2b70c"
},
{
"spdxElementId": "SPDXRef-f2d426372356602d",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-7516f5d905deb6db"
},
{
"spdxElementId": "SPDXRef-35c3680577fae0df",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-780fcf6f56cca2e0"
},
{
"spdxElementId": "SPDXRef-35c3680577fae0df",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-ab2d028a906db5df"
},
{
"spdxElementId": "SPDXRef-35c3680577fae0df",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-8e69e89855b5ae0f"
},
{
"spdxElementId": "SPDXRef-35c3680577fae0df",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-d59e19c68624688f"
},
{
"spdxElementId": "SPDXRef-35c3680577fae0df",
"relationshipType": "CONTAINS",
"relatedSpdxElement": "SPDXRef-757b30be1d3baa0b"
}
]
}
![]()
![]()
![]() --scope all-layers
--scope all-layers
![]() -o
-o