Cluster API k3s
Cluster API bootstrap provider k3s (CABP3) is a component of Cluster API that is responsible for generating a cloud-init script to turn a Machine into a Kubernetes Node; this implementation brings up k3s clusters instead of full kubernetes clusters.
CABP3 is the bootstrap component of Cluster API for k3s and brings in the following CRDS and controllers:
- k3s bootstrap provider (KThrees, KThreesTemplate)
Cluster API ControlPlane provider k3s (CACP3) is a component of Cluster API that is responsible for managing the lifecycle of control plane machines for k3s; this implementation brings up k3s clusters instead of full kubernetes clusters.
CACP3 is the controlplane component of Cluster API for k3s and brings in the following CRDS and controllers:
- k3s controlplane provider (KThreesControlPlane)
Together these two components make up Cluster API k3s...
Testing it out.
Warning: Project and documentation are in an early stage, there is an assumption that an user of this provider is already familiar with ClusterAPI.
Prerequisites
Check out the ClusterAPI Quickstart page to see the prerequisites for ClusterAPI.
Three main pieces are
-
Bootstrap cluster. In the
samples/azure/azure-setup.shscript, I use k3d, but feel free to use kind as well. -
clusterctl. Please check out ClusterAPI Quickstart for instructions.
-
Infrastructure Specific Prerequisites:
- For more Azure information go to CAPZ Getting Started
- For more AWS information go to CAPA Getting Started
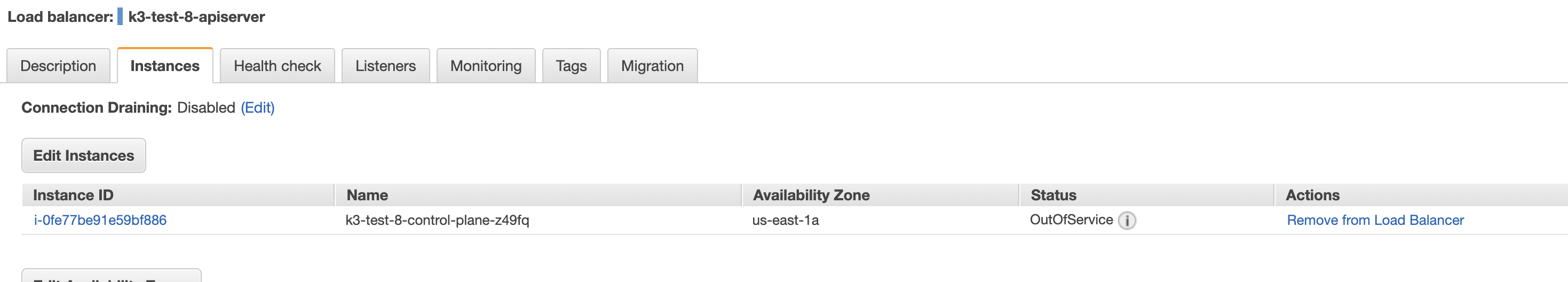
Cluster API k3s has been tested on AWS, Azure, and AzureStackHCI environments.
To try out the Azure flow, fork the repo and look at samples/azure/azure-setup.sh.
To try out the AWS flow, fork the repo and look at samples/aws/aws-setup.sh.
Known Issues
Roadmap
- Support for External Databases
- Fix Token Logic
- Setup CAPV samples
- Clean up Control Plane Provider Code
- Post an issue!