CVE-2021-26084
this is a script written in golang to exploit Confluence OGNL Injection [CVE-2021-26084].
git clone https://github.com/march0s1as/CVE-2021-26084/
cd CVE-2021-26084
go get -v github.com/fatih/color
go build post.go
./post.go -h
HiveNightmare this is a quick and dirty exploit for HiveNightmare (or SeriousSam) - CVE-2021–36934 This allows non administrator users to read the SAM
CVE-2021-3449 OpenSSL 1.1.1k DoS exploit Usage: go run . -host hostname:port This program implements a proof-of-concept exploit of CVE-2021-3449 affe
Golang-CVE-2021-22205-POC A bare bones CVE-2021-22205 Gitlab RCE POC written in Golang which affects Gitlab CE/EE 13.10.3 Gitlab CE/EE 13.9.6 Gitl
CVE-2021-22205 CVE-2021-22205 RCE 工具仅用于分享交流,切勿用于非授权测试,否则与作者无关 -R string VPS to load tools eg: -R 127.0.0.1:8083 -T string Tool nam
CVE-2021-41277 Usage 1. show help info ~/CVE-2021-41277 ❯ go run main.go -h Usage of main: -f string File containing li
CVE-2021-43798 Grafana 8.x Path Traversal (Pre-Auth) All credits go to j0v and his tweet https://twitter.com/j0v0x0/status/1466845212626542607 Disclai
CVE-2021-44228-Test-Server A small server for verifing if a given java program is succeptibel to CVE-2021-44228 Usage Build the program using go build
CVE-2021-41277 PoC Metabase is an open source data analytics platform. Local File Inclusion issue has been discovered in some versions of metabase. He
log4shelldetect Scans a file or folder recursively for jar files that may be vulnerable to Log4Shell (CVE-2021-44228) by inspecting the class paths in
hi dude
the script doesnt work
/_/\ Confluence OGNL injection ( o.o ) > CVE-2021-26084 <
^ <
[+] starting the exploit [+] enjoy your shell >:)
like a magic ~> whoami like a magic ~>
REALITY_SMASHER vRealize RCE + Privesc (CVE-2021-21975, CVE-2021-21983, CVE-0DAY-?????) "As easy to stop as it is to comprehend." What is it? "Reality
PewSWITCH A FreeSWITCH specific scanning and exploitation toolkit for CVE-2021-37624 and CVE-2021-41157. Related blog: https://0xinfection.github.io/p
poc-cve-2021-4034 PoC for CVE-2021-4034 dubbed pwnkit Compile exploit.go go buil
CVE-2021-4034 January 25, 2022 | An00bRektn This is a golang implementation of C
CVE-2021-29156 Proof-of-Concept (c) 2021 GuidePoint Security Charlton Trezevant [email protected] Background Today GuidePoint
jndi-ldap-test-server This is a minimalistic LDAP server that is meant for test vulnerability to JNDI+LDAP injection attacks in Java, especially CVE-2
proxylogscan This tool to mass scan for a vulnerability on Microsoft Exchange Server that allows an attacker bypassing the authentication and imperson
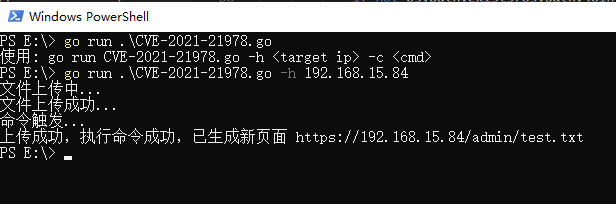
CVE-2021-21978 CVE-2021-21978 RCE exp 影响版本 VMware View Planner Harness 4.X 与 CVE-2021-21978 类似,该漏洞可以在未授权访问的情况下,上传任意文件,并通过修改自带 py 脚本实现远程代码执行。
CVE-2021-26855 CVE-2021-26855 ssrf 简单利用 golang 练习 影响版本 Exchange Server 2013 小于 CU23 Exchange Server 2016 小于 CU18 Exchange Server 2019 小于 CU7 利用条件 该漏洞不
CVE-2021-26855 CVE-2021-26855 ssrf 简单利用 golang 练习 影响版本 Exchange Server 2013 小于 CU23 Exchange Server 2016 小于 CU18 Exchange Server 2019 小于 CU7 利用条件 该漏洞不